SSH Reverse Tunneling Power Secrets Serving Web Servers From Home.
In this wild guide we show how ssh can be used to to punch your home server out to the public internet!

On top of this excellent guide there is another entire guide that goes in detail into all the fun stuff that you can do with SSH sessions!

Secure Shell is a very powerful tool for making encrypted links. 99% of the tutorials really focus on remote shell access to machines. But that is where they end. But the potential is WAY higher.
Consider the following:
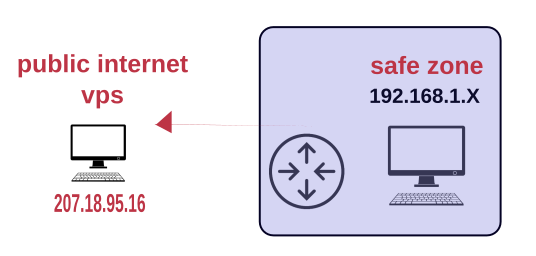
- Users can almost never serve from home as their home router times out.
- ISP providers use hidden Port Overloading. What that means is you don't really have your own IP. You share it.
- Typically users end up paying for providers and installing custom applications so they can 'bring their machine out of the 'safe zone'
- Users can initiate a ssh connection from their home machine to a public VPS, and they can have the ssh kept alive with the ssh command line option:
-o ServerAliveInterval=15But what if..

Did you know that you can also,
- Reverse Tunnel your home http server to the internet facing VPS in a single command?
- It was able to run a entire ghost blog insider a docker container from a home computer address, yet it had a fully qualified domain name running through a reverse proxy - onto the reverse tunnel of the ssh to the docker container and the entire thing worked!
First - You have to build your ssh tunnel.
ssh -v -N -o ServerAliveInterval=15 -R 8082:localhost:8080 root@207.18.95.16Understand that.. ssh is trunking non-ssh traffic, aka any traffic through the pipe, http traffic, https, dns, you get the idea. (whoa!)
Yes you can! This is effectively saying the following sets of options. Let's go over them.
-v - Verbose Mode
-N- Do not login when you ssh into the remote machine.
-o ServerAliveInterval=15- Keep the connection alive by sending data test packets every 15 seconds.
-R 8082:localhost:8080- Reverse tunnel. In this instance we are going to open port 8082 at the remote location that is going to pipe to port 8080 on the home machine. It must be understood that there is a container ready, and listening at port 8080 (ghost blog as an instance).
root@207.18.95.16- The machine that is going to open port 8082, which is going to pipe all the traffic it receives to port 8080 on the other end of the tunnel
To make this work you will need to modify your /etc/ssh/sshd_config for:
AllowAgentForwarding yes
AllowTcpForwarding yes
GatewayPorts yes
PermitTunnel yes
But wait there is more!

Install your standard reverse proxy manager (nginx) - we recommend the following guide: here
Once you have it setup, and you have your domain name forwarding to your IP cleanly in your A records setup, it is simply a matter of executing the above Reverse Shell - then setting up your Nginx proxy as follows:
In the following I have set up a Reverse Proxy Host, that forwards to the port that SSH Reverse Tunnel is listening on. Let us review:
- This is crazee. You have turned your dollar-store VPS into nothing more than a serving router.
- DNS servers receive a call for www.someplace.com. The browser if asking for a http connection will automatically call that domain IP with port 80. If the browser asks for a https connection it will automatically ask for port 443.
- NGINX is listening on those two ports (80, 443) and has a forwarding qualification from www.someplace.com to http://107.152.41.231:8082 which the reverse tunnel is connected to with its SSH reverse-tunnel pipe.
- The http connection is now routed to port 8082 which is then tunnelled through the SSH back to the 192.168.0.N ip address at port 8080 the local ghost instance.
- The local ghost instance itself is also running inside a docker container which adds more security.
The entire process is seamless. Because one can now use their home address, which can run a docker ghost blog - which can all be sub-domains of a main domain.
Caveat. This is not for the faint of heart. Know what you are doing, any public facing server typically receives millions of hacks a day. If your equipment gets breached, and all your personal stuff ends up in some foreign land.
The implications of what this means is literally staggering. It costs significantly to host high-memory / high-core machines - we are talking $80/month. Especially high-memory or high-ssd setups. But by doing this one can have a LOT of horsepower tucked away piping through the SSH boxes. It would allow you to run your own AI generating entire sites at fractional costs of other players.
If you want a guide of the ghost blog side setup consider this:



