dragonOS: console tool: aircrack-ng
In this post we cover some of the tools found in dragonOS - namely aircrack-ng!

- Only use these tools in a legal and ethical manner.
- aircrack-ng has a dedicated page: https://www.aircrack-ng.org/
- It should be understood that it is a companion tool to airodump-ng which will collect and save .ivs packets and aircrack-ng which will work on the files offline.
- Add a wireless device that is not configured on any WLAN network.
- Plug it in and make sure that Linux automatically loaded the drivers you need, if not:
Part 1: Get your wireless device to work (and in Monitor Mode)
Drivers can be tricky for off-market 802.11ac dongles. Amazon has piles of these but usually they have some third-party driver etc, especially with RealTek clones.
- To see the raw connection (when you plug a device into the USB)
sudo desg -w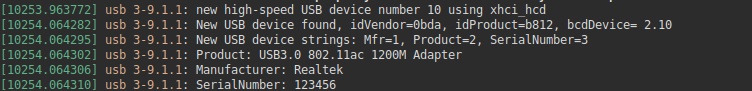
- For many realtek drivers try.
sudo apt install git dkms
git clone https://github.com/cilynx/rtl88x2bu.git
sudo dkms add ./rtl88x2bu
sudo dkms install rtl88x2bu/5.8.7.1- For a short list of devices:
sudo nmcli device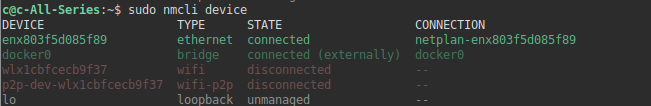
- For nmcli detailed device list
sudo nmcli device show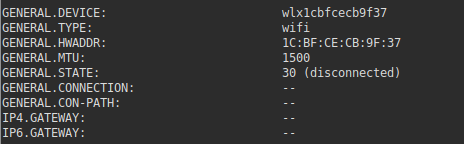
- For iw list
sudo iw dev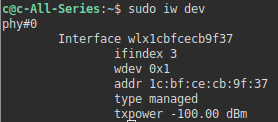
Getting your device into monitor mode is required in order for it to be able to do the environmental survey. One uses ifconfig to take the device down, then iwconfig to set mode monitor then ifconfig to bring it back up.
sudo ifconfig wlx1cbfcecb9f37 down
sudo iwconfig wlx1cbfcecb9f37 mode monitor
sudo ifconfig wlx1cbfcecb9f37 upNow you can try a wireless environmental scan with
sudo airodump-ng start wlx1cbfcecb9f37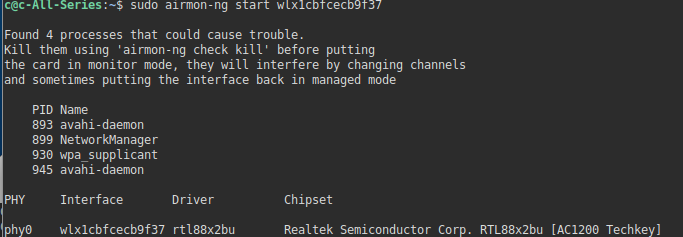
You can see this actually fails as other devices are implementing control hooks to solve this use:
sudo airmon-ng check killYou can see several devices were competing and the big one is wpa_supplicant.
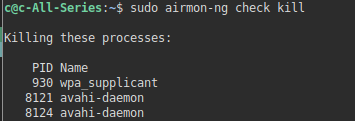
Because one ends up doing this frequently one can make a script to batch all of it in one shot.
Bigger TroubleShooting. In some cases avahi-daemon and wpa_supplicant were constantly putting the device into station mode (that would disable scanning) Finally they were simply disabled with:
sudo systemctl mask wpa_supplicant.server
sudo systemctl disable wpa_supplicant
sudo systemctl stop wpa_supplicant
sudo systemctl mask avahi-daemon
sudo systemctl disable avahi-daemon
sudo systemctl stop avahi-daemon2. Environmental Scan and (IVS Packet Collection)
In the end airmon-ng simply was not working with this device, but a second one did work - airodump-ng, here is how to scan.
sudo airodump-ng -i -w captures.dat --output-format csv <wireless device>This command will automatically submit your survey and save it in a CSV file for aircrack-ng. What it will also do is save the .ivs packets (-i) It is recommended to add the --bssid <bssid> so that you are only collecting packets that you require.
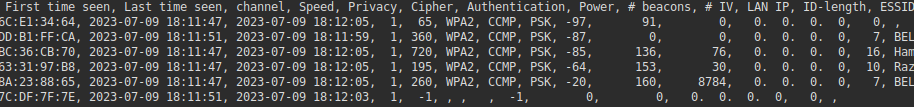
3. Running aircrack-ng
Finally you have your .ivs packets of your vector and you need to run it against your wordlists or pick a suitable cracking method. One can get the infamous 'rockyou.txt' password list which was a large list of compromised passwords kept in the clear from here. Additionally you may need to send de-auth packets which is outside the scope of this guide but covered here
aircrack-ng -w rockyou_1.txt captures.dat-02.ivsCommand Line Options:
Aircrack-ng 1.6 - (C) 2006-2020 Thomas d'Otreppe
https://www.aircrack-ng.org
usage: aircrack-ng [options] <input file(s)>
Common options:
-a <amode> : force attack mode (1/WEP, 2/WPA-PSK)
-e <essid> : target selection: network identifier
-b <bssid> : target selection: access point's MAC
-p <nbcpu> : # of CPU to use (default: all CPUs)
-q : enable quiet mode (no status output)
-C <macs> : merge the given APs to a virtual one
-l <file> : write key to file. Overwrites file.
Static WEP cracking options:
-c : search alpha-numeric characters only
-t : search binary coded decimal chr only
-h : search the numeric key for Fritz!BOX
-d <mask> : use masking of the key (A1:XX:CF:YY)
-m <maddr> : MAC address to filter usable packets
-n <nbits> : WEP key length : 64/128/152/256/512
-i <index> : WEP key index (1 to 4), default: any
-f <fudge> : bruteforce fudge factor, default: 2
-k <korek> : disable one attack method (1 to 17)
-x or -x0 : disable bruteforce for last keybytes
-x1 : last keybyte bruteforcing (default)
-x2 : enable last 2 keybytes bruteforcing
-X : disable bruteforce multithreading
-y : experimental single bruteforce mode
-K : use only old KoreK attacks (pre-PTW)
-s : show the key in ASCII while cracking
-M <num> : specify maximum number of IVs to use
-D : WEP decloak, skips broken keystreams
-P <num> : PTW debug: 1: disable Klein, 2: PTW
-1 : run only 1 try to crack key with PTW
-V : run in visual inspection mode
WEP and WPA-PSK cracking options:
-w <words> : path to wordlist(s) filename(s)
-N <file> : path to new session filename
-R <file> : path to existing session filename
WPA-PSK options:
-E <file> : create EWSA Project file v3
-I <str> : PMKID string (hashcat -m 16800)
-j <file> : create Hashcat v3.6+ file (HCCAPX)
-J <file> : create Hashcat file (HCCAP)
-S : WPA cracking speed test
-Z <sec> : WPA cracking speed test length of
execution.
-r <DB> : path to airolib-ng database
(Cannot be used with -w)
SIMD selection:
--simd-list : Show a list of the available
SIMD architectures, for this
machine.
--simd=<option> : Use specific SIMD architecture.
<option> may be one of the following, depending on
your platform:
generic
avx512
avx2
avx
sse2
altivec
power8
asimd
neon
Other options:
-u : Displays # of CPUs & SIMD support
--help : Displays this usage screen

